User Management
Creating Users
Creating, editing and deleting users is performed in the Administrator application in the Users table (see Figure 1).
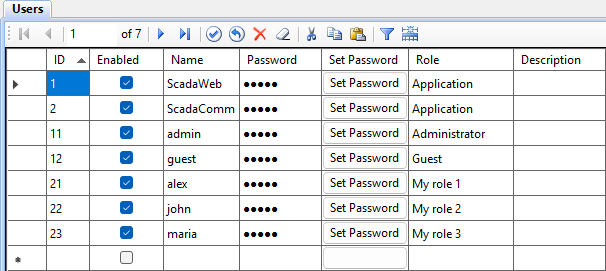
Users with IDs from 1 to 12 are created by default from the project template. The ScadaWeb and ScadaComm users are intended to connect the Webstation and Communicator client applications to the Server application. The admin and guest users who use the built-in roles are intended to log in to the system. The alex, john and maria users who use custom roles are created as an example.
Rights Assignment
Rights are assigned to roles on objects. Note that rights are assigned only for custom roles. For built-in roles, permission check is already implemented in applications. A role is a named set of rights.
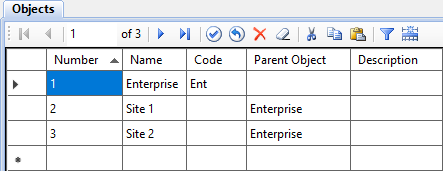
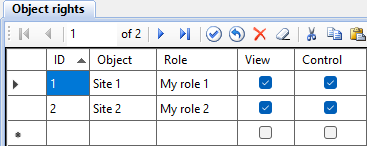
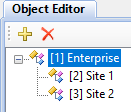
Before assigning rights, fill in the Objects and Roles tables (see Figures 2 and 3). Next, specify the rights in the Object rights table (see Figure 4). Objects can relate to each other hierarchically (see Figure 5). If a top-level object has certain permissions, they are inherited by lower-level objects.
Built-in Roles
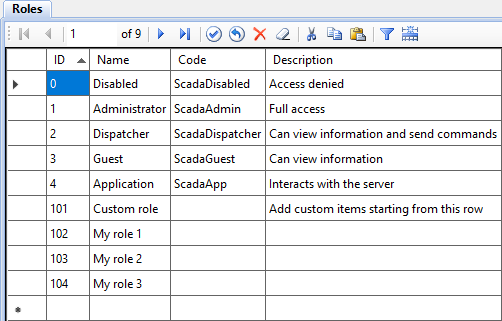
Built-in roles whose permissions are hard-coded into the applications are listed in the following table.
| ID | Name | Description |
|---|---|---|
| 0 | Disabled | Access denied |
| 1 | Administrator | Full access |
| 2 | Dispatcher | Can view information and send commands |
| 3 | Guest | Can view information |
| 4 | Application | Interacts with the server |
Features of the built-in roles:
- Their IDs are from 0 to 4.
- They apply to all objects.
- Cannot be changed.
Custom Roles
Custom roles are roles created by the project developer. In the example above, the custom roles are My role 1, My role 2, and My role 3.
It is recommended to assign IDs to custom roles starting from 101. The Code field of a role is intended for integration with third-party systems and databases. If integration is not used, the code can be left blank.
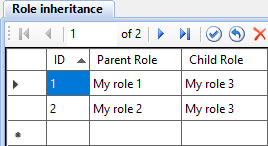
By using the role inheritance mechanism, it is possible to significantly reduce the number of records that are added to the Object rights table.
In the Role inheritance table shown in Figure 6, the child role My role 3 inherits from the parent roles My role 1 and My role 2 the sum of the rights of both.
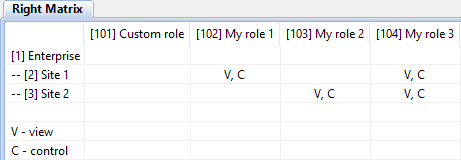
To check whether the rights are configured properly, open the Rights Matrix window (see Figure 7), which is called by the  button located on the toolbar of the Administrator application. The figure below shows how role inheritance works.
button located on the toolbar of the Administrator application. The figure below shows how role inheritance works.